How to Secure Your Home Wireless Network
by Howard Fosdick
Updated: 2024 Originally published in OSNews
This tutorial tells how to secure your home wireless network. Good security means implementing a series of small steps to progressively lock down a system. There is no single "silver bullet." Add up all the small steps and you'll have a reasonably secure system.
Why care about security? If someone steals your bandwidth that leaves less for you. But there's more. In the U.S., the courts sometimes rule that home network addresses (IP addresses) uniquely identify individuals. You could be held responsible if someone uses your wireless network -- without your knowledge or permission -- to illegally download music, movies, or software.
And yet some routers do not ship with all the most secure defaults. It's on you! Hence this tutorial.
I'll walk you through how to secure your home network manually. This ensures you'll understand it. That's important because all manufacturers have different setup panels and use different terminology. Our goal is to ensure you'll be able to recognize and set the key security options whatever router you have.
Okay, let's get started.
Turn Off Unused Wireless
It should go without saying, but if you don't need wireless to access your network, disable it. Even if you disable wireless, you still need to secure the router! So keep reading.Also: don't make a wireless router a more available target than it need be. Turn it off when it's not in use.
Turn Off Wifi-Protected Setup (WPS)
Most routers offer easy-to-use Setup Wizards. These are helpful -- but make sure yours lets you set all the security options I list in this article. If it doesn't, go back and manually update the missing settings to be more secure.Some routers also offer fully automated set up. An older one called Wi-Fi Protected Setup had a serious security defect. Disable it! You should be able to do this by simply adding or removing a checkmark from the WPS option.
A new automated setup procedure called Wi-Fi Easy Connect eventually replaced WPS. It's secure, so use it if you like.
Use Only Secure Routers and Wireless Devices
Ensure your wireless router and all your devices support current
communications protocols. These are the common IEEE 802.11
wireless standards you'll encounter:| 802.11 Standard: |
B | G | N | AC | AX | BE |
| Year: | 2000 | 2003 | 2007 | 2013 | 2021 | 2024 |
| Security: | BAD! | Old | Old | Best | Best | Best |
| Encrypt Modes: |
WEP | WPA2, WPA, more | WPA2, WPA, more | WPA3, WPA2, more | WPA3, WPA2, more | WPA3, WPA2, more |
You'll often see these standards noted on routers or their packaging in this manner: 802.11n or 802.11ac.
For the best security, all routers, laptops, and other devices on your network should use either at least the AC standard or better. N and earlier standards do have security flaws.
The B standard supports an obsolete encryption method that crackers can break in minutes, called WEP encryption. If you have some really old equipment you're still using, you need to be aware that old B routers are completely insecure. You really should toss out any old B router and buy a newer secure one!
Router Security Settings
Now let's securely configure a wireless router. The exact options
and terminology you'll encounter vary by brand but you should be
able to locate the right settings on your router. They'll appear in
either drop-down list boxes or textual entry blanks. I'll show
common Linksys and D-Link terminology in my examples. A tip first. While you can immediately change wireless settings for devices, sometimes a quick reboot helps. Especially when configuring a wireless laptop, a quick shutdown and restart sometimes fixes a problem that can otherwise vex you.
SSID -- First, you assign your new wireless router a network name, better known as a Service Set Identifier or SSID. Assign an SSID that someone can not easily identify or guess. A52c481757bc is better than Joe_Fox. Do not keep the default name of Linksys or dlink or whatever.
Write down the SSID for later. You may have to enter it into the network connection definition for each wireless device that will connect to this router when you set up its networking configuration.
Here's how to enter the SSID on Linksys and D-link routers:
Linksys:
Wireless Network Name (SSID): ______________
orD-Link:
Wireless Network Name: ______________ (Also called
the SSID)
Disable SSID Broadcasting. Next, disable the automatic broadcasting of your SSID name. Unless you do, the router continually bleats its name out to the world. The only use for this is to help someone who doesn't know your network is there to notice it, and then to try and get on it. Disabling SSID broadcasting alone does not stop crackers any more than assigning an unusual SSID (for reasons I won't go into here), nevertheless it is one of the many steps you should take to enhance Wi-Fi security.
To turn off SSID broadcasting:
Linksys:
Wireless SSID Broadcast: ___ Enable
_x_ Disable
orD-Link:
Enable Hidden Wireless: _x_ (Also called the
SSID Broadcast)
Since your router is not broadcasting its presence and name, you'll have to manually enter the SSID or network name into the network connection definition for each device that will wirelessly connect with this router. You only have to do this one time for each device, when you first set up its wireless connection.
If you have a laptop client configuration tool that only configures for broadcast SSIDs, enable SSID broadcasting on the router, configure the laptop for access, then disable SSID broadcasting on the router. The client will now be able to access the router even though it doesn't broadcast its SSID.
Router Password -- Assign a tough password to the router to block unauthorized users. Good passwords are long and contain intermixed letters, digits, and special characters. The router's HELP panel will tell you its password rules. You can enter any password into the free online Password Strength Checker to find how crackable it is.
USER
ID: __network-name__ PASSWORD: __your-password__
Most routers allow you to create both the user ID and its corresponding password, so you would enter:
USER
ID: __your-user-id__ PASSWORD: __your-password__
Every cracker knows all the router default SSID's, user ids, and passwords. Assign strong new ones!
Wired Administration Only -- This setting ensures that only a physically connected computer can access the router configuration panels. So the router can not be remotely configured by wireless even if someone has the password. This is excellent security, because it means that someone can not remotely access your administration panels -- they would have to get physically inside your house to do that.
So set this option:
Linksys:
Remote Management: ___ Enable _x_
Disable
orD-Link:
Enable Remote Management: ___
Remember -- If you always use a wireless laptop, this means that if you ever want to reconfigure the router again, you'll have to physically attach your laptop by wire to the router to make changes.
Authentication and Encryption
Authentication refers to how a router verifies the legitimacy of a wireless device that tries to connect to it and establishes a connection.Encryption refers to the securely coded communications between the router and the wireless device once it's connected.
Routers support various authentication and encryption standards. Your goal is to use the strongest methods supported by your router and the wireless devices that use it. Here are common levels, from weakest to strongest. Not all routers support all options:
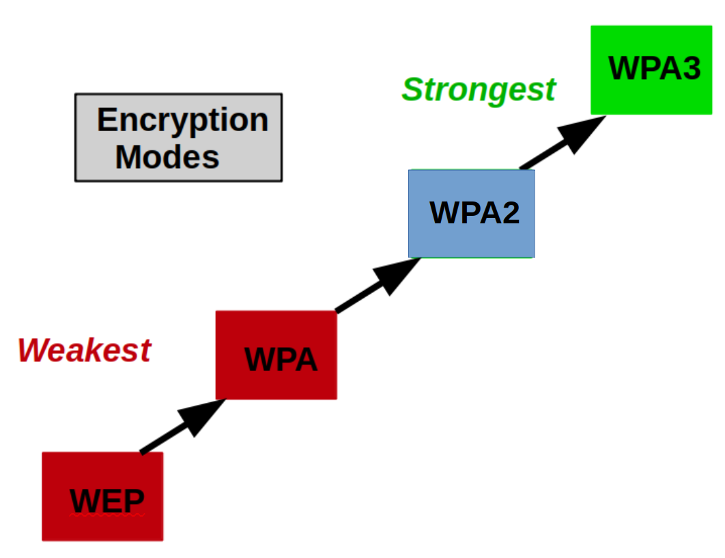
Routers usually have a drop-down list box where you select this standard. It's labeled something like Security Mode or Encryption Mode or Authentication.
Unfortunately router vendors use different terms to refer to the same standards. I'll list most the terms you might encounter below and show how they are equivalent. You'll have to pick out the specific term your router uses.
WPA3 is the best standard. It was introduced in late 2018. Its SAE (Simultaneous Authentication of Equals) feature replaces the PSK (Pre-Shared Key) authentication method used in prior WPA versions.
Set your router to the best setting it supports:
| Evaluation: | Standard: | Usually Labeled As: |
| Best | WPA3 | WPA3 Personal, WPA3-SAE |
| Acceptable | WPA2 | WPA2 Personal, WPA2-PSK2, WPA-PSK |
| Bad | WPA | WPA Personal,WPA-PSK, WPA Shared Key |
| Bad (never use) |
WEP | WEP 64-bits, WEP 128-bits, WEP Shared Key |
| Bad (never use) |
Open | WEP Open System, No encryption, None |
Unless your goal is to share your internet with the world, do not use WEP, No Security, Open System, or None.
Options containing the words Enterprise or RADIUS are typically used by businesses using RADIUS servers, so you normally wouldn't use them for a home network.
The Password -- Next, you'll need to enter a password value that will become the basis for encryption. It will be labeled something like:
- Password
- Shared Key
- Passphrase (a phrase that automatically generates a password for you)
When you set up your wireless client devices, you'll also enter this value into their Network Configuration definition. This is why this value is often called a shared key -- it is shared between the router or modem and your wireless clients.
The Encryption Algorithm -- In addition to setting the router's authentication level and encryption key, you'll have to tell the router the kinds of wireless devices it will support and their encryption algorithms. Select from the table below. Not all routers support all settings:
| Setting: | Use When: | |
| Best | AES | Your router and all your wireless devices support WPA3 or WPA2. |
| Only if necessary | AUTO --or-- TKIP+AES |
You have a mixed set of wireless devices. The router will use the encryption standard appropriate to each wireless device. For a more secure network, get rid of those old TKIP devices! |
| Bad | TKIP | Your router and/or your wireless devices use WPA. |
AES is best. Since nearly all devices made in the past decade support it, it should be your choice.
Some routers will ask you whether you want to support AC, N, G and/or B wireless devices. Ideally, you have only AC devices. Remember, if you have any B devices, they are completely insecure.
Remaining Router Security Settings
MAC Address Filtering -- Every wireless device or laptop has a unique Media Access Control Address, or MAC Address.Many routers offer a feature called MAC address filtering, by which you can either allow or disallow wireless devices with specific MAC addresses. This feature ensures that only the wireless devices you specify are allowed to use your router.
To set this up, you need to know the MAC address of every laptop or wireless device you want to use your router. Then enter it into the router's panel of allowable MAC addresses.
Most laptops have a sticker underneath or on the wireless card that will tell you the MAC address. Or use enter a software command to determine it:
| Windows line command: | ipconfig /all (look for the Physical Address of your wireless connection) |
| Linux line command: | ifconfig -a (look for the HWaddr value for your wireless connection) |
| Mac OS GUI: | System Preferences ->Network -> pick proper Location -> AirPort -> see the AirPort ID |
| iPhone GUI: | Settings -> General -> About > see the Wi-Fi Address |
A typical MAC address appears as a series of hexadecimal values in one of these formats:
00:14:F3:19:66:F0
--or-- 00-14-F3-19-66-F0
--or-- 0014F31966F0
Enter the MAC addresses of all your wireless devices into the MAC Address Filter table in the router's configuration panels, then tell the router to only accept communications from these addresses. Voila!
Ping Response -- A ping is an anonymous request that comes into your router and asks for a response. Respond to an anonymous internet request? Not a good idea. Tell your router not to respond:
Linksys:
Block Anonymous Internet Requests: _x_
orD-Link:
Enable WAN Ping Respond: ___
Firewall -- Routers come with an embedded firewall. Ensure it is enabled. It should be by default. Some routers allow you to specify rules or otherwise configure the firewall. This is very router-specific so I won't cover it here. The default configuration is usually adequate.
Firmware Update -- The software embedded in your router is called firmware. Most routers allow you to automatically perform a firmware update across the web. This increases security if vendors fix firmware bugs or add security features since the router shipped. So be sure to update your router.
Be certain the update occurs without interruption! Never turn off the router or computer during the update or otherwise interrupt the update. This could mess up your router's firmware or even make it unusable.
Channels -- A channel is a radio frequency used for wireless communication between your router and its wireless clients. Routers typically offer channels 1 through 11. Channel 6 is the usual default. Other routers default to auto channel scan or auto channel selection, which means the router dynamically determines the channel to use.
The purpose of having multiple channels is to find a frequency that is free from interference with other devices (your cordless phone, game box, etc). From the security standpoint, the channel is irrelevant. I usually pick a channel other than 6 just because it's less common. Remember that the router and wireless devices that use it must be set to use the same channel!
Wisdom
There is no single silver bullet for a router security. But if you follow these recommendations you'll have a home network that is as secure as you can possibly make it.Read more in Wikipedia articles on Wi-Fi, wireless security, wireless LAN security, and the WPA standards.
------------------------------
Howard Fosdick is an independent consultant who supports databases and operating systems.
Router Security Checklist
You can use this checklist to ensure that you've set all the most secure router settings:
| Completed: | Option: | Recommended Setting: |
| ____ | BE, AX, AC, N , G, or B router | AC or better routers are current. Replace any obsolete B router immediately! |
| ____ | Wireless enabled | Set to Off or Disable if you don't use wireless devices. |
| ____ | SSID | Assign a unique complex SSID (network name). |
| ____ | SSID Broadcast | Disable (default is often Enable). |
| ____ | Router password | Assign unique complex router password. |
| ____ | User or Admin id | Assign unique complex router user id if the SSID is not used as the login user id. |
| ____ | Wired administration only | Enable. This means anyone (including you) can only update the router with a physically connected device going forward. It's much more secure. |
| ____ | Remote administration | Disable. This means anyone (including you) can only update the router with a physically connected device going forward. It's much more secure. |
| ____ | Encryption protocol | Use WPA3 (or WPA2 if you must). Don't pick WPA. Never use WEP or Open System or None -- unless you wish to share your internet with everyone. |
| ____ |
WPA algorithm | Use AES. Don't select AUTO unless you have to, as it could use less-secure TKIP for certain devices. |
| ____ | MAC Address Filtering | Enable (the default is "Disabled" or "not used"). You'll have to enter the MAC address of each of your devices into the router, but doing so enhances security. |
| ____ | Ping Response | Disable. |
| ____ | Firewall | Enable. |
| ____ | Firmware update | Recommended. |
| ____ | Channel | I pick a lesser-used channel, but it's not really that relevant to security. |
====> Like this free article? Please spread the link love to Slashdot, LXer, or wherever. Thank you!